Hunting the Hackers: Tracking Intrusions in Azure DevOps
Have you ever thought, What makes the security of software development and collaboration platforms a paramount challenge for SOC analysts in today’s rapidly advancing technological world?
Today the world has the most advanced technology and it is continuously growing therefore the security of a software development and collaboration platforms is of paramount importance and it is a crucial challenge for SOC analysts. Let’s talk about Azure DevOps, which is a leading cloud-based platform, plays an important role in enabling organizations to streamline their software development lifecycle and achieve Continuous Integration and Continuous Deployment (CI/CD). However, as with any digital environment, security is a critical concern.
Analyzing Hacker Tactics in Azure DevOps:
In this article, we will explore three real-world scenarios commonly employed by hackers to gain unauthorized access and implement persistence and execution techniques within Azure DevOps. We will examine how Security Operations Centers (SOC) can proactively monitor and defend against such activities by implementing analytical rules. The scenarios include:
01- New PAT added to Azure DevOps
02- Azure DevOps Pipeline Created and Deleted on the same day
03- Azure DevOps Audit Stream Disabled
Before delving into the creation of “The Hunt,” let’s take a moment to discuss the aforementioned scenarios along with their corresponding detection techniques.
Scenario-01: New PAT added to Azure DevOps:
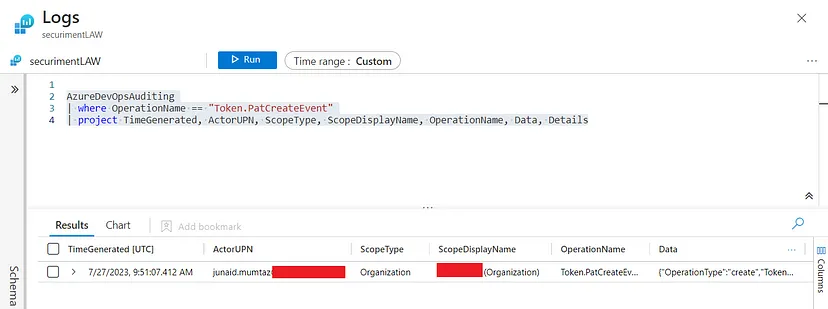
1.1- KQL Query:
The Azure Sentinel detection technique for identifying this behavior can be accomplished using the following Kusto Query Language (KQL) query:
AzureDevOpsAuditing
| where OperationName == "Token.PatCreateEvent"
|project
TimeGenerated,
ActorUPN,
ScopeType,
ScopeDisplayName,
OperationName,
Data,
Details
1.2- Detection Results:
Scenario-02: Azure DevOps Pipeline Created and Deleted on the same day:
Monitoring Azure DevOps pipelines created and deleted on the same day is crucial for SOC analysts due to potential security risks associated with initial unauthorized access. When a hacker gains access, such as through a compromised Personal Access Token (PAT) or other credentials, they can exploit this opportunity to carry out malicious activities.
One of the primary concerns is that the attacker may create pipelines and inject malicious code or scripts into these tasks. This allows them to execute their nefarious agenda, potentially compromising the integrity and security of the software development process. They could even use these pipelines to inject artifacts into other legitimate pipelines, making it harder to detect their malicious actions.
Scenario-02: Azure DevOps Pipeline Created and Deleted on the same day:
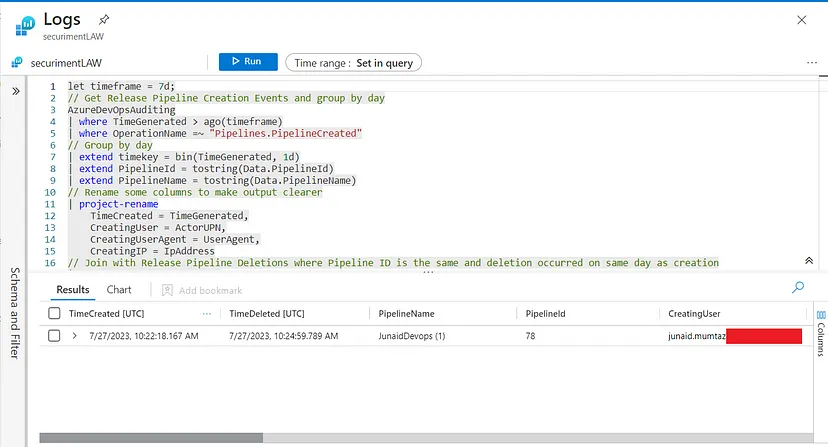
The Azure Sentinel detection technique for identifying this behavior can be accomplished using the following Kusto Query Language (KQL) query:
let timeframe = 7d;
// Get Release Pipeline Creation Events and group by day
AzureDevOpsAuditing
| where TimeGenerated > ago(timeframe)
| where OperationName =~ "Pipelines.PipelineCreated"
// Group by day
| extend timekey = bin(TimeGenerated, 1d)
| extend PipelineId = tostring(Data.PipelineId)
| extend PipelineName = tostring(Data.PipelineName)
// Rename some columns to make output clearer
| project-rename
TimeCreated = TimeGenerated,
CreatingUser = ActorUPN,
CreatingUserAgent = UserAgent,
CreatingIP = IpAddress
// Join with Release Pipeline Deletions where Pipeline ID is the same and deletion occurred on same day as creation
| join (AzureDevOpsAuditing
| where TimeGenerated > ago(timeframe)
| where OperationName =~ "Pipelines.PipelineDeleted"
// Group by day
| extend timekey = bin(TimeGenerated, 1d)
| extend PipelineId = tostring(Data.PipelineId)
| extend PipelineName = tostring(Data.PipelineName)
// Rename some things to make the output clearer
| project-rename
TimeDeleted = TimeGenerated,
DeletingUser = ActorUPN,
DeletingUserAgent = UserAgent,
DeletingIP = IpAddress)
on PipelineId, timekey
| project
TimeCreated,
TimeDeleted,
PipelineName,
PipelineId,
CreatingUser,
CreatingIP,
CreatingUserAgent,
DeletingUser,
DeletingIP,
DeletingUserAgent,
ScopeDisplayName,
ProjectName,
Data,
OperationName,
OperationName1
| extend
timestamp = TimeCreated,
AccountCustomEntity = CreatingUser,
IPCustomEntity = CreatingIP
2.2- Detection Results:
Scenario-3: Azure DevOps Audit Stream Disabled:
Okay, imagine we’re dealing with some threat actors! First, they created something called PAT and they played around with a Pipeline, creating it and then deleting it, that’s execution attempt number one, according to the mysterious Mitre attack techniques. But now, here come the tricky hackers! They want to hide and stay undetected, so they use something called Defense Evasion techniques. These tricks help them avoid getting caught and stop the safety measures that the organizations put in place.
So, what did these hackers do? Well, they made the audit logs in Azure DevOps disappear! It’s like hiding all the evidence so that nobody knows what they’ve been up to. When the security people try to look at the logs, they can’t find anything useful, like timestamps or signs of suspicious activity. It’s like trying to solve a puzzle without all the pieces!
So, the battle is on! The hackers think they’re clever, but the security team won’t back down. They’ll use their skills and tools to protect the digital world from these troublemakers. Here is the KQL to detect this suspicious behaviour.
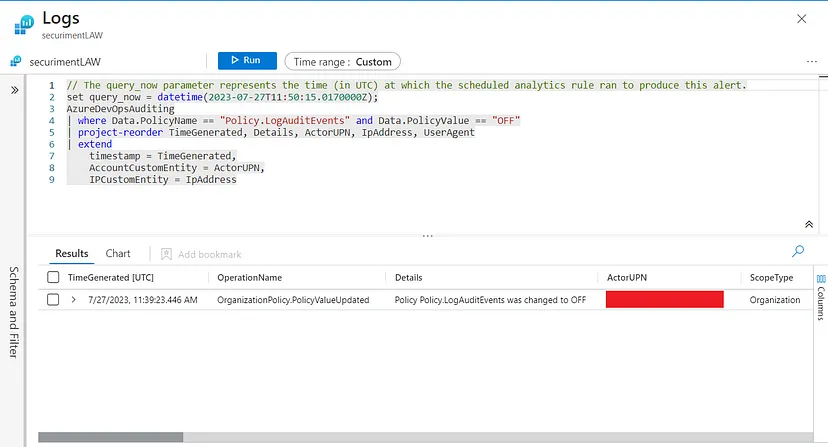
3.1- KQL Query:
Following Query can be used for identifying this behavior.
AzureDevOpsAuditing
| where Data.PolicyName == "Policy.LogAuditEvents" and Data.PolicyValue == "OFF"
| project-reorder
TimeGenerated,
Details,
ActorUPN,
IpAddress,
UserAgent
| extend
timestamp = TimeGenerated, AccountCustomEntity = ActorUPN, IPCustomEntity = IpAddress
3.2- Detection Results:
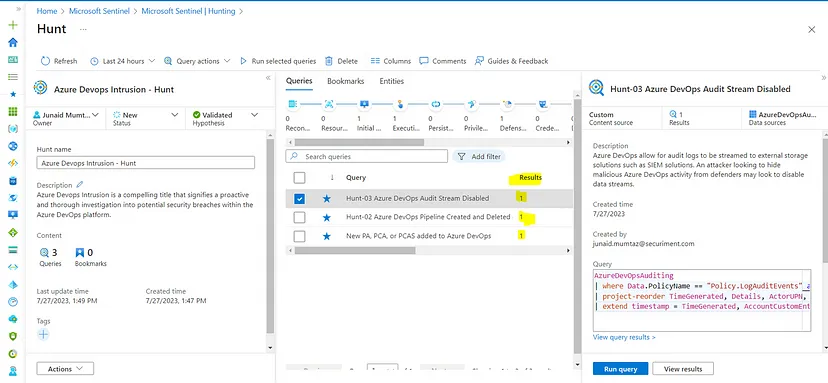
The HUNT (Preview):
Get Excited for the Cyber Adventure with Azure Sentinel’s “The Hunt”! It’s Not a Movie, but a Super Secure DevOps Quest to Uncover Sneaky Hackers. Grab Your Popcorn and Let’s Catch Those Cyber Critters! Lights, Camera, Action!”
Let’s first define what is actually the Hunt in Azure Sentinel.
Azure Sentinel hunts enables users to seek out undetected threats and malicious behaviors in an organized way by creating a hypothesis, searching through data, validating that hypothesis, and acting when applicable. You can also create new analytic rules, TI, and incidents based on findings.
Microsoft Learn provides a comprehensive guide on creating an Azure Sentinel Hunt, which we won’t delve into here. However, I’d be glad to share the Hunt I’ve created for all the scenarios mentioned above.
The Hunt involves running the hunting queries, which can either be built-in or written from scratch. You have the flexibility to execute queries individually or all at once. Typically, in a threat campaign, there will be multiple actions, each generating an event. Hunting queries are created based on these events, and several hunting queries combined form a single entity known as The Hunt.
Let’s revisit the previous scenarios. I’ve consolidated all three use cases into a single hunt called “Azure DevOps Intrusion.” This hunt is designed to detect any intrusion attempts in Azure DevOps. It keeps an eye out for the creation of new Personal Access Tokens (PATs), which could indicate a potential intrusion. Additionally, it monitors the creation and deletion of pipelines using these PATs. Finally, the hunt tracks unauthorized access that may attempt to remove traces or artifacts from the system. By encompassing all these activities, the hunt ensures comprehensive monitoring of intrusion attempts in Azure DevOps, eliminating the need to define individual use cases separately.
Now, armed with the ability to take action and run logic app workflows (playbooks) on each entity, we can mitigate the attack surface while also saving the precious time of a SOC analyst.
Isn’t it a wonderful option for effectively monitoring our infrastructure? Embracing automation in our security measures certainly has its perks!
Latest News
Every week we publish exclusive content on various topics.